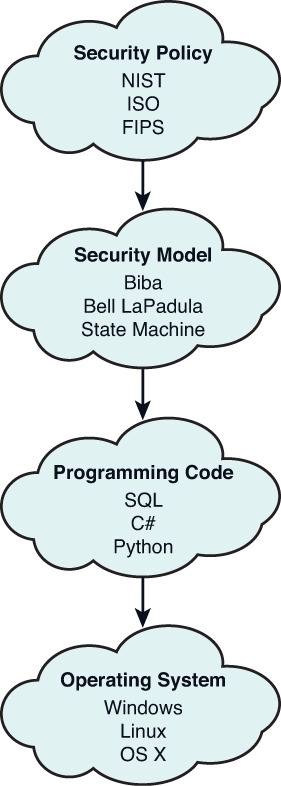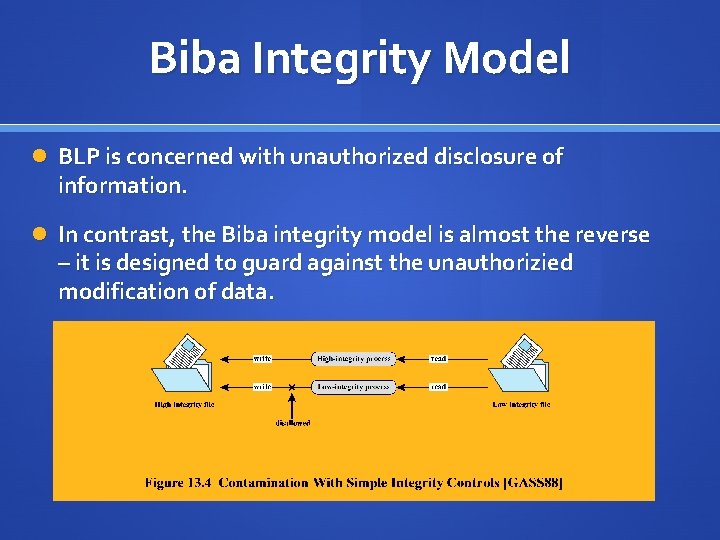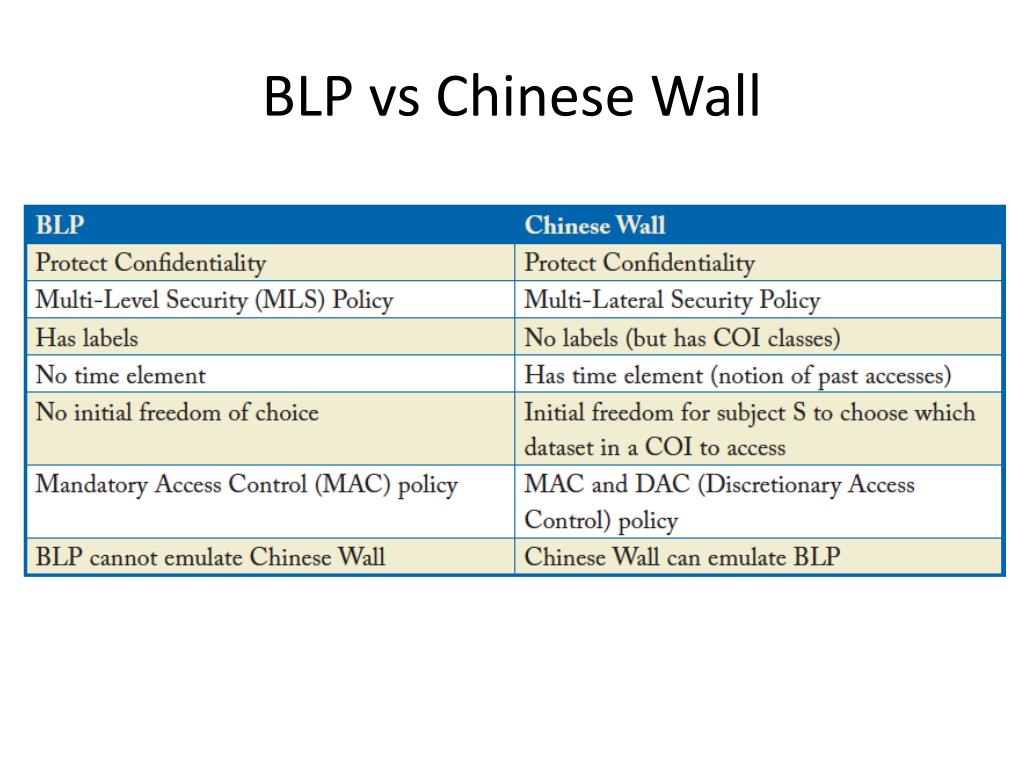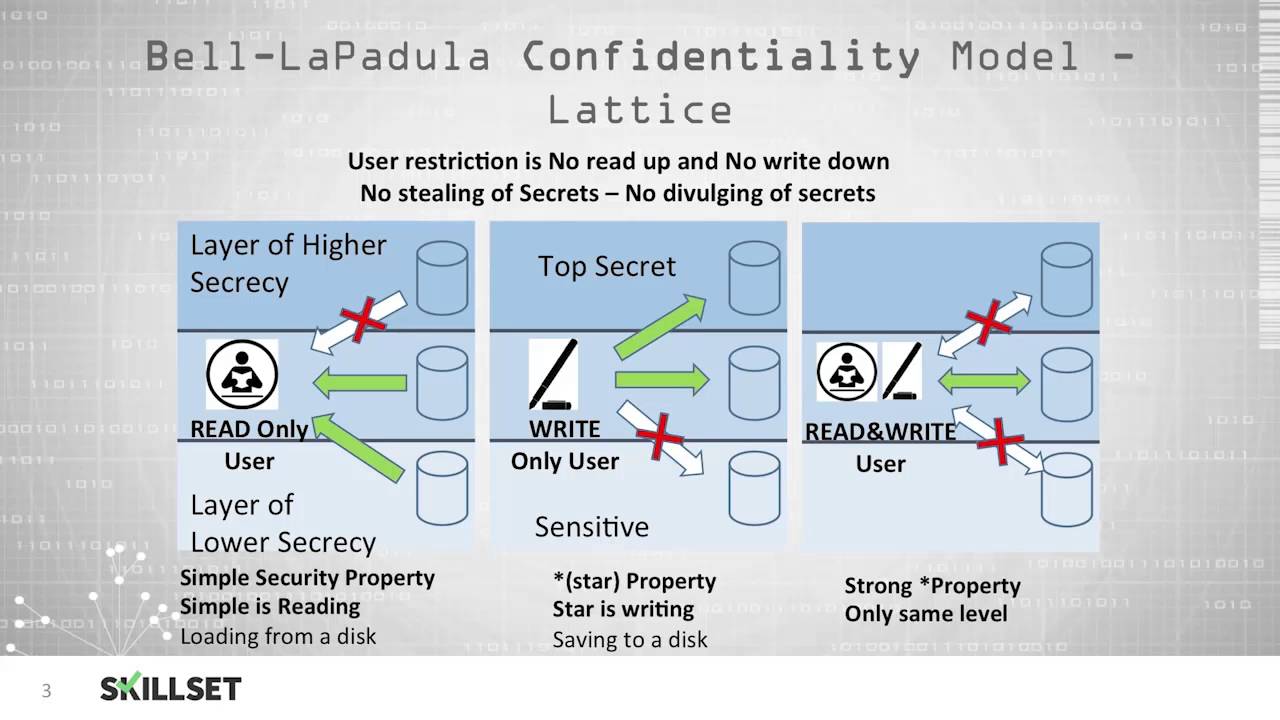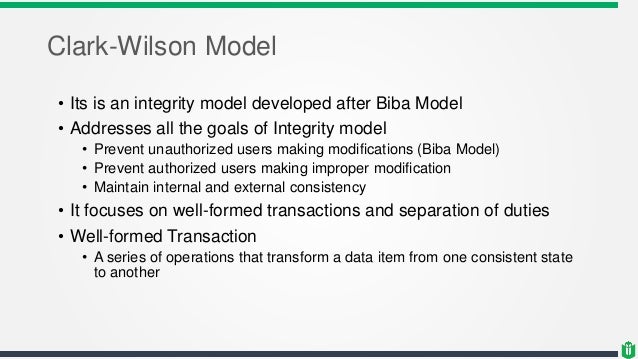
Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram

Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

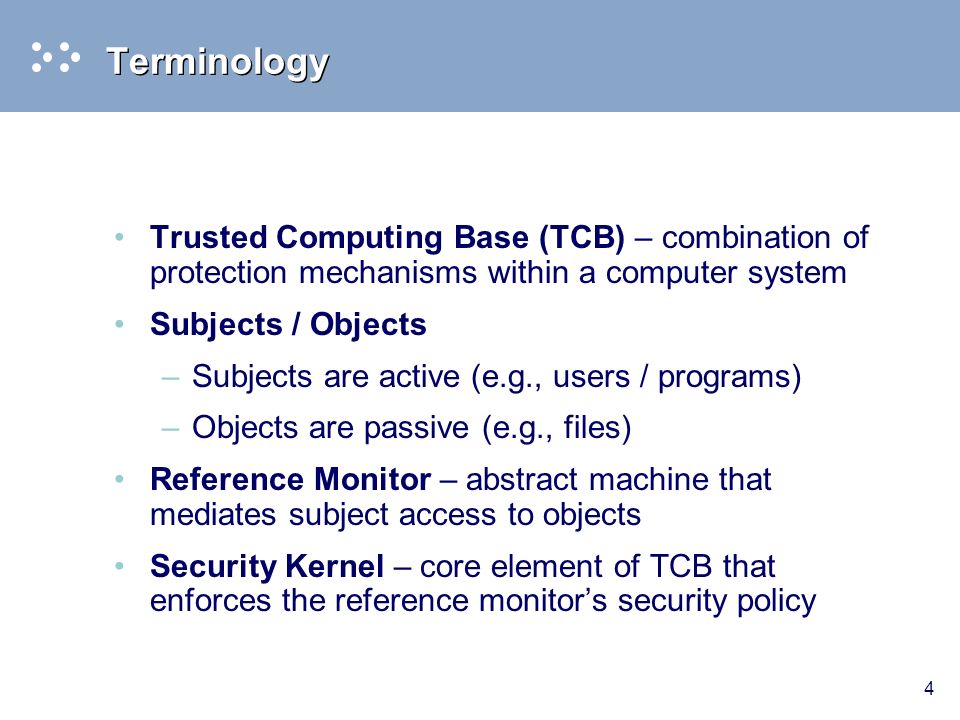
Lecture 2: Security Policy Models Fred Chong CS290N Architectural Support for Secure and Reliable Computing. - ppt download

Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download